How To Remove Tiny Banker Trojan
What is Tinynuke?
Tinynuke (likewise known as Nukebot) is a trojan-blazon application that collects account credentials. Tinynuke hijacks browsers and gathers data when users visit banking websites. After its initial release in late 2022, Tinynuke was being sold on various hacker forums, however, in early 2022, the entire source code was leaked and, therefore, the malware became publicly accessible.
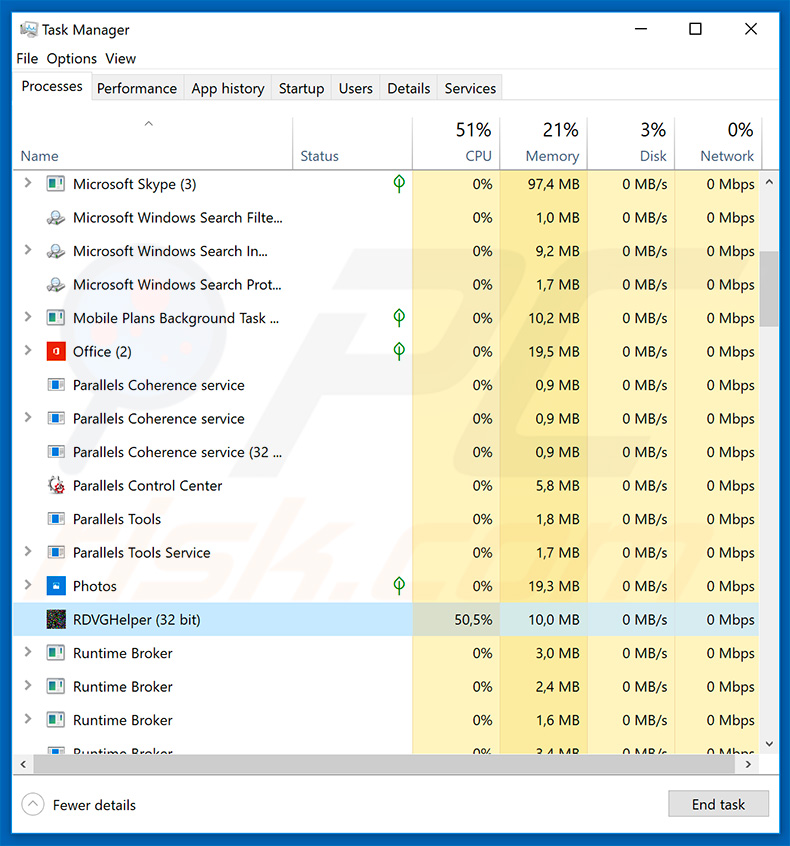
Tinynuke malware overview
Research shows that Tinynuke injects JavaScript into sure banking company websites (including Amazon and Lloyds bank). In addition, Tinynuke collects HTTP Mail service request data from Net Explorer, Google Chrome, and Mozilla Firefox. This is washed to gather various account credentials, peculiarly targeting bank accounts.
Cyber criminals aim to generate as much acquirement equally possible and are probable to misuse hijacked accounts through online purchases, money transfers, and then on. Therefore, victims might encounter serious financial loss.
Furthermore, many users are frequently careless, lack cognition in cyber security, and often use the same login details (emails) and passwords for multiple accounts. Thus, afterwards gaining access to one account, criminals are often able to admission a number of others. Email, social networks and other similar accounts can be used to steal the victim's identity.
These criminals might send malicious files to the victim's contacts or attempt to infringe money, thereby causing fifty-fifty more than issues. In summary, the presence of Tinynuke trojan can lead to serious privacy problems and pregnant fiscal loss (debts, lost savings, etc.).
Tinynuke is often promoted using spam e-mail campaigns. Therefore, if you have recently opened suspicious attachments or see dubious processes (east.g., such as "RDVGHelper") in Windows Task Managing director, immediately scan the organisation with a reputable anti-virus/anti-spyware suite and eliminate all detected threats.
| Name | Tinynuke malware |
| Threat Type | Trojan, password-stealing virus, cyberbanking malware, spyware. |
| Detection Names | Avast (Win32:BankerX-gen [Trj]), Combo Cleaner (DeepScan:Generic.Tinukebot.one.E874ED70), ESET-NOD32 (A Variant Of Win32/Tinukebot.C), Kaspersky (UDS:DangerousObject.Multi.Generic), Microsoft (Trojan:Win32/Ymacco.AA5B), Full List Of Detections (VirusTotal) |
| Malicious Procedure Name(s) | RDVGHelper (process name may vary) |
| Symptoms | Trojans are designed to stealthily infiltrate the victim'due south computer and remain silent, and thus no particular symptoms are clearly visible on an infected car. |
| Distribution methods | Infected e-mail attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Harm | Stolen passwords and banking information, identity theft, the victim's calculator added to a botnet. |
| Malware Removal (Windows) | To eliminate possible malware infections, browse your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. |
Information-stealing malware examples
In that location are many trojan-type infections that share similarities with Tinynuke. For instance, TrickBot, Adwind, FormBook, then on. Although the developers are dissimilar, these programs take virtually identical behavior - all collect data. Therefore, they pose a significant threat to your privacy and financial safe. Eliminating infections such equally Tinynuke immediately.
How did Tinynuke infiltrate my reckoner?
A distribution method used by cyber criminals is spam email campaigns. They send deceptive electronic mail messages (e.g., fake invoices/bills for certain orders) and encourage users to open them. This results in system infections. Ane of the campaigns we analyzed sent emails with links to invoices regarding the refurbishment of a Samsung Tv.
The e-mail independent a Dropbox link to download the zipper, which was presented every bit a Microsoft Word document (invoice). In fact, this was an executable called "Invoice_260319_9lz8kba2e.DOC.exe". In this way, users tin can finish up infecting their computers manually.
Spam email campaigns commonly proliferate trojans such as Tinynuke, still, criminals are as well likely to spread these infections using fake software updaters/cracks and unofficial software download sources. Simulated updaters infect computers by exploiting outdated software bugs/flaws or only downloading and installing malware rather than the updates.
Nifty tools activate paid software free of accuse, however, since they are often used to proliferate malware, users ordinarily infect their computers, rather than gaining access to paid features. Peer-to-Peer (P2P) networks, freeware download websites, free file hosting sites, and similar, are used to proliferate malware past presenting it as legitimate software.
As with e-mail attachments, users are tricked into manually downloading and installing malware. In summary, the main reasons for computer infections are lack of knowledge of these threats and careless beliefs.
How to avoid installation of malware?
To prevent this situation, be very cautious when browsing the internet and downloading, installing, and updating software. Never open electronic mail attachments that exercise not concern you (are irrelevant), or if the sender is unrecognizable/suspicious. Download software from official sources only, using direct download links.
Third party downloaders/installers should not be used, since they oftentimes include rogue apps. Keeping installed applications and operating systems updated is as well extremely of import, however, use implemented functions or tools provided by the official programmer. Be aware that software piracy is a cyber crime and the chance of infection is extremely high.
Therefore, never try to crack installed apps. Lastly, have a reputable anti-virus/anti-spyware suite installed and running - these tools detect and eliminate malware earlier the system is harmed. If you lot believe that your computer is already infected, we recommend running a scan with Philharmonic Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Case of a spam e-mail entrada promoting a download link of a malicious attachment that injects the Tinynuke trojan:
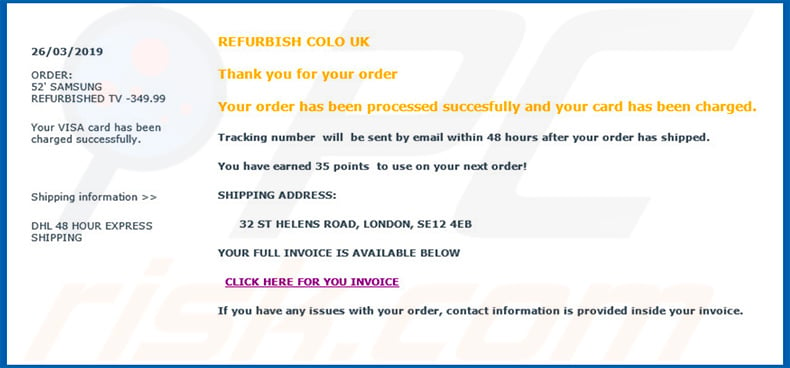
Text presented within this e-mail:
Society:
52' SAMSUNG REFURBISHED TV -349.99
Your VISA menu has been charged successfully.
Shipping data >>
DHL 48 HOUR Express SHIPPING
REFURBISH COLO Uk
Thank yous for your gild
Your order has been candy succesfully and your carte du jour has been charged.
Tracking number volition be sent by email within 48 hours later your society has shipped.
You have earned 35 points to use on your next order!
Aircraft ADDRESS:
32 ST HELENS ROAD, LONDON, SE12 4EB
YOUR FULL INVOICE IS Available Below
CLICK Hither FOR YOU INVOICE
If you have whatever bug with your society, contact information is provided inside your invoice.
Screenshot of the malicious attachment download on a Dropbox website:

Update December 14, 2022 - Tinynuke trojan has been observed being leveraged almost exclusively against French entities. The target list is broad, ranging from manufacturing, structure, technology, to finance organizations and companies. These campaigns involve Tinynuke proliferation via invoice-themed and other business concern-related spam emails. The infection chain consists of links nowadays in the spam letters, leading to malicious websites that are also in French. From said sites, victims obtain archived files that comprise Tinynuke.
Instant automatic malware removal: Manual threat removal might be a lengthy and complicated process that requires avant-garde computer skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to become rid of malware. Download information technology by clicking the push button beneath:
▼ DOWNLOAD Combo Cleaner Past downloading any software listed on this website y'all agree to our Privacy Policy and Terms of Use. To use full-featured production, y'all have to buy a license for Philharmonic Cleaner. 7 days free trial available. Philharmonic Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Quick carte du jour:
- What is Tinynuke?
- STEP 1. Manual removal of Tinynuke malware.
- Footstep 2. Cheque if your computer is make clean.
How to remove malware manually?
Transmission malware removal is a complicated task - ordinarily information technology is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If y'all wish to remove malware manually, the outset pace is to identify the name of the malware that you are trying to remove. Hither is an example of a suspicious program running on a user's computer:
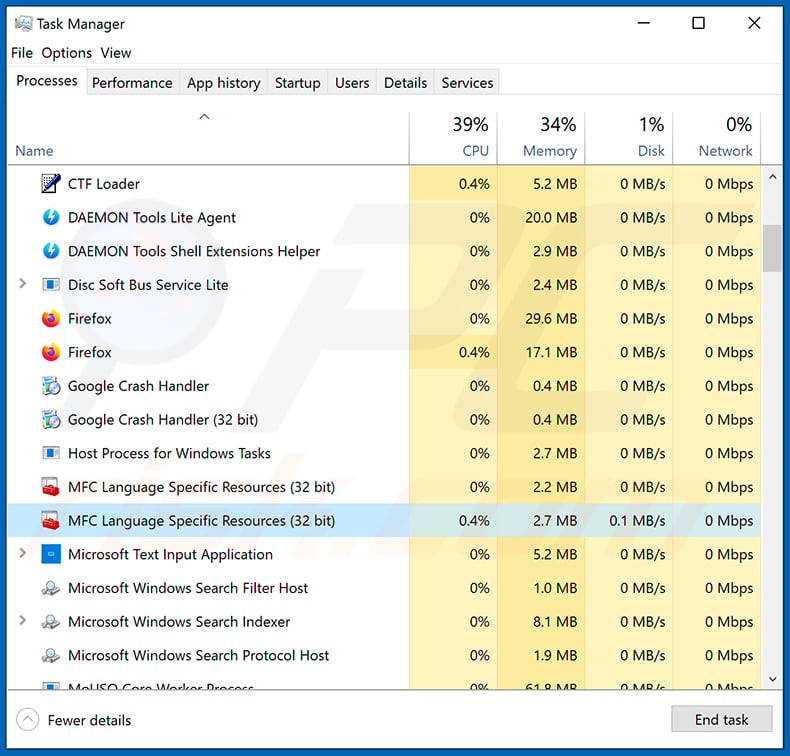
If you checked the list of programs running on your calculator, for case, using task manager, and identified a programme that looks suspicious, you should continue with these steps:
 Download a plan called Autoruns. This programme shows auto-start applications, Registry, and file organization locations:
Download a plan called Autoruns. This programme shows auto-start applications, Registry, and file organization locations:
 Restart your computer into Condom Mode:
Restart your computer into Condom Mode:
Windows XP and Windows seven users: Get-go your computer in Condom Mode. Click Start, click Shut Down, click Restart, click OK. During your calculator starting time process, press the F8 key on your keyboard multiple times until yous see the Windows Advanced Selection menu, and and so select Safe Way with Networking from the list.
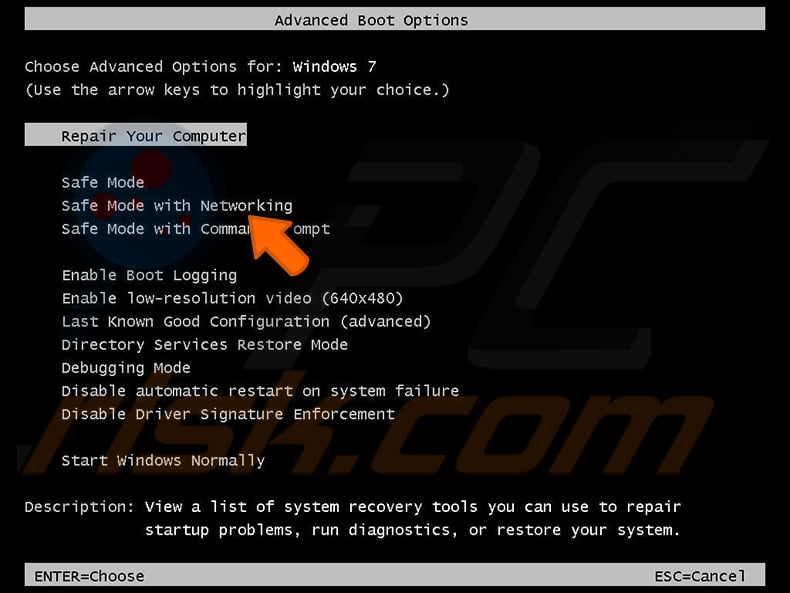
Video showing how to start Windows seven in "Safe Mode with Networking":
Windows eight users: Kickoff Windows 8 is Safe Way with Networking - Go to Windows viii Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Avant-garde startup.
Click the "Restart now" button. Your calculator will at present restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" push. In the advanced choice screen, click "Startup settings".
Click the "Restart" button. Your PC volition restart into the Startup Settings screen. Press F5 to boot in Prophylactic Manner with Networking.
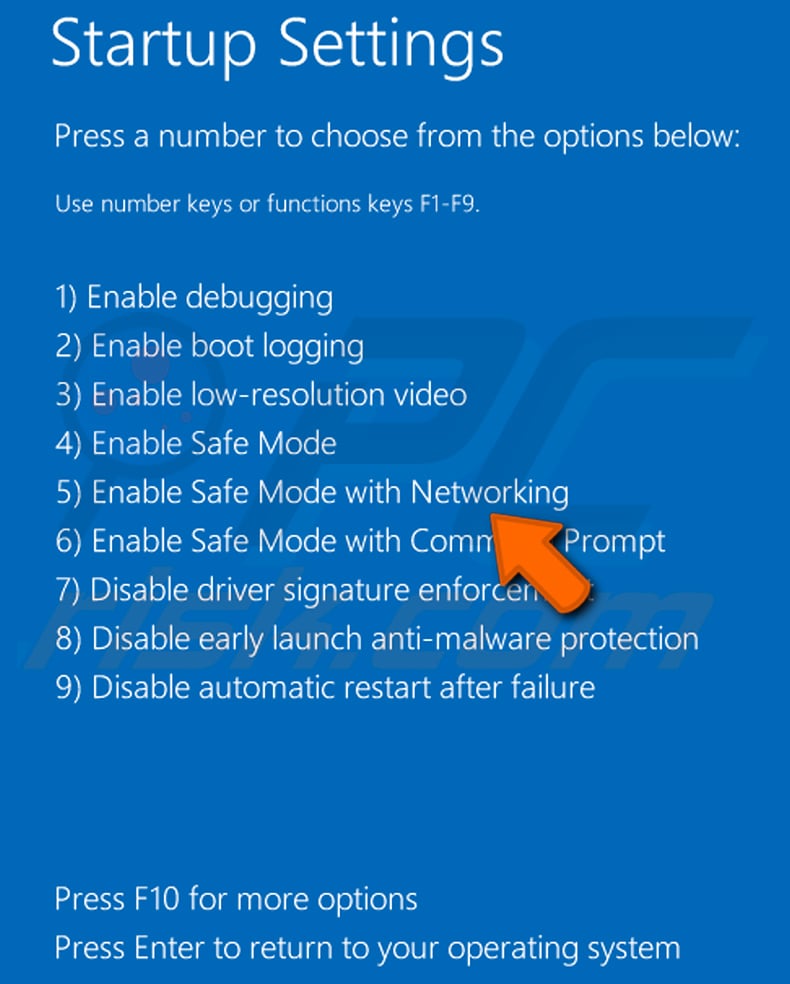
Video showing how to kickoff Windows viii in "Safe Manner with Networking":
Windows 10 users: Click the Windows logo and select the Ability icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", side by side select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the post-obit window you should click the "F5" push on your keyboard. This will restart your operating arrangement in safe mode with networking.
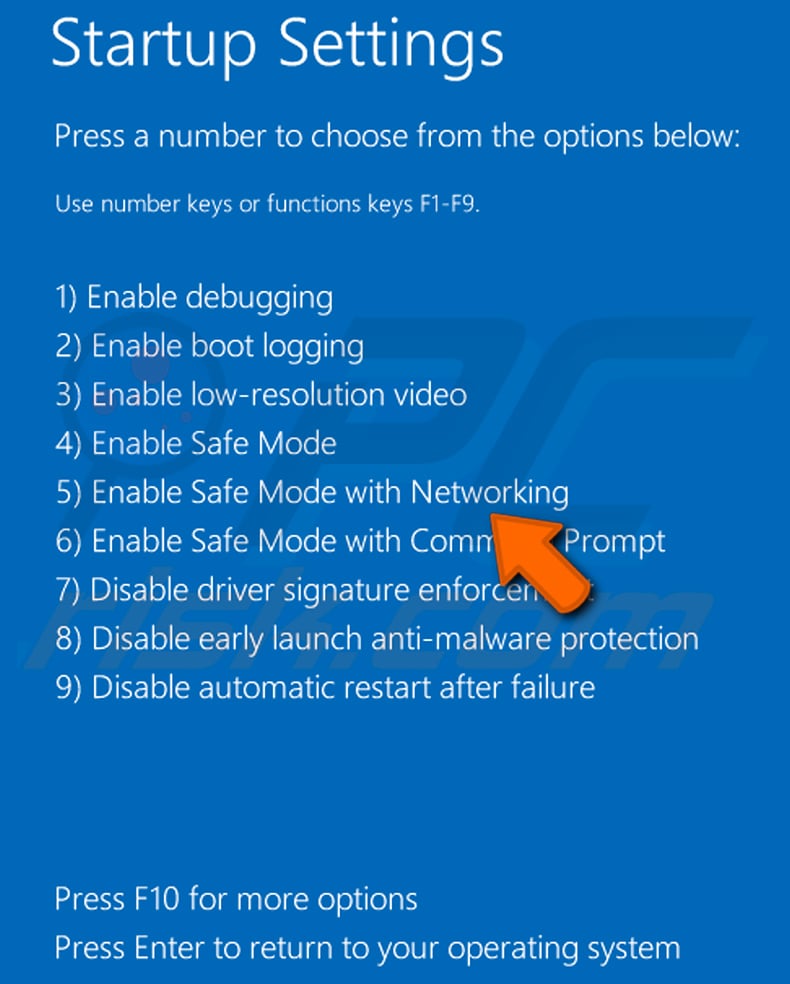
Video showing how to commencement Windows 10 in "Safe Way with Networking":
 Extract the downloaded annal and run the Autoruns.exe file.
Extract the downloaded annal and run the Autoruns.exe file.
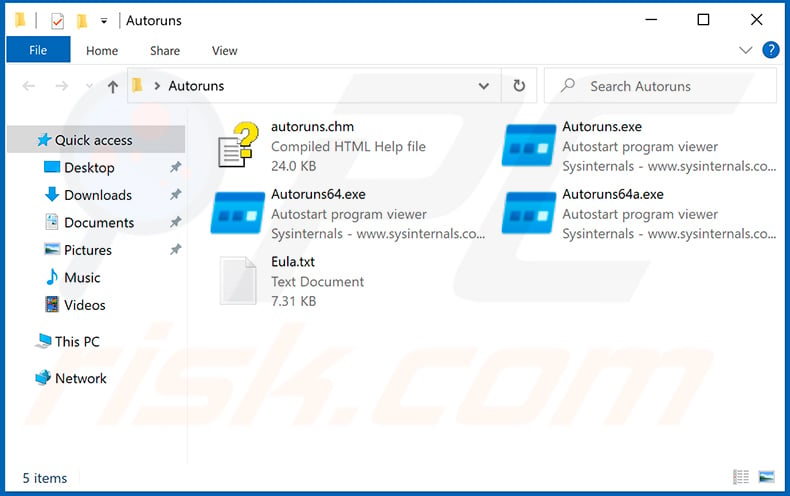
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
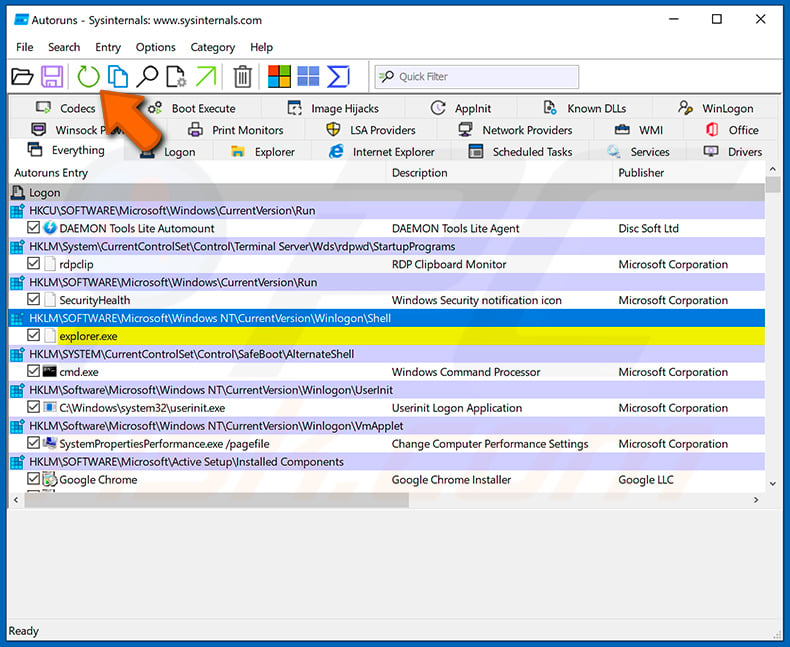
 Check the list provided by the Autoruns awarding and locate the malware file that you desire to eliminate.
Check the list provided by the Autoruns awarding and locate the malware file that you desire to eliminate.
You should write down its full path and name. Note that some malware hides procedure names under legitimate Windows process names. At this phase, it is very important to avert removing arrangement files. Later on you locate the suspicious program you wish to remove, correct click your mouse over its name and choose "Delete".
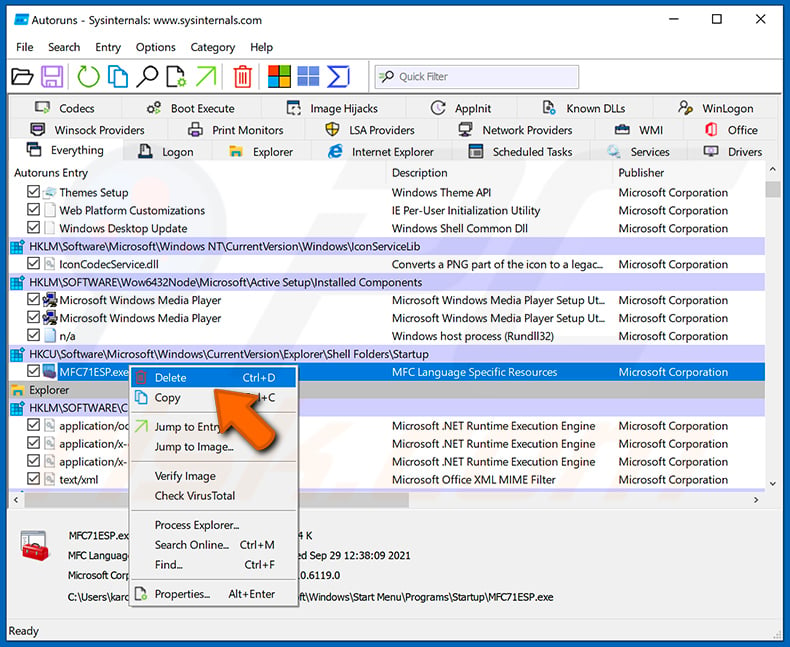
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next organisation startup), you should search for the malware proper name on your estimator. Be sure to enable subconscious files and folders before proceeding. If you discover the filename of the malware, be sure to remove information technology.
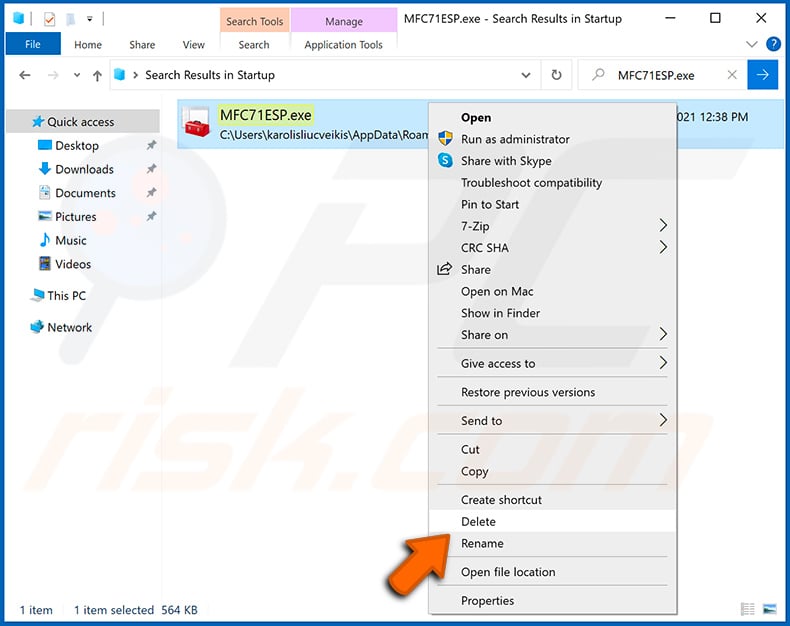
Reboot your estimator in normal style. Following these steps should remove whatever malware from your computer. Note that manual threat removal requires advanced computer skills. If yous do not accept these skills, get out malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. Every bit always information technology is best to foreclose infection than try to remove malware later. To go along your reckoner safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning information technology with Philharmonic Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with Tinynuke malware, should I format my storage device to get rid of information technology?
No, Tinynuke'south removal does not require such drastic measures.
What are the biggest issues that Tinynuke malware tin can cause?
The threats posed past a malicious program depend on its capabilities and the cyber criminals' aims. Tinynuke is an information-stealing trojan; hence, about of the dangers it poses chronicle to privacy. For example, Tinynuke infections can lead to severe privacy issues, access/control loss over online accounts, identity theft, and significant financial losses.
What is the purpose of Tinynuke malware?
Typically, malicious software has the sole purpose of generating revenue for its developers/ the cyber criminals using it. Other potential goals include: the criminals' amusement, political/geopolitical motivations, personal reasons (i.e., targeting specific individuals), process disruption (east.g., website, service, company, organisation, etc.), and so along.
How did Tinynuke malware infiltrate my computer?
Malware is proliferated using phishing and social technology tactics. For example, malicious programs are distributed through drive-by (deceptive and stealthy) downloads, spam emails, online scams, unofficial and freeware websites, Peer-to-Peer sharing networks, illegal software activation ("cracking") tools, fake updates, and then on.
Volition Combo Cleaner protect me from malware?
Yes, Philharmonic Cleaner is capable of detecting and eliminating nearly all of the known malware infections. However, it is noteworthy that performing a full system scan is critical - since high-end malicious software tends to hibernate deep within systems.
Well-nigh the writer:

Tomas Meskauskas - expert security researcher, professional malware analyst.
I am passionate about figurer security and technology. I have an feel of over 10 years working in various companies related to reckoner technical issue solving and Cyberspace security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed almost the latest online security threats. Contact Tomas Meskauskas.
PCrisk security portal is brought by a company RCS LT. Joined forces of security researchers assistance educate computer users about the latest online security threats. More information about the visitor RCS LT.
Our malware removal guides are free. Still, if you lot want to support us you can ship the states a donation.
Source: https://www.pcrisk.com/removal-guides/14761-tinynuke-banking-trojan

0 Response to "How To Remove Tiny Banker Trojan"
Post a Comment